80 if (argc == ARG_NUM) {
81 sigNo = strtoul(argv[0], &endPtr, 0);
83 PRINT_ERR(
"\nsigNo can't access %s.\n", argv[0]);
87 pidNo = strtoul(argv[1], &endPtr, 0);
89 PRINT_ERR(
"\npidNo can't access %s.\n", argv[1]);
93 ret =
OsKill(pidNo, abs(sigNo), OS_USER_KILL_PERMISSION);
94 HILOG_INFO(LOG_CORE,
"Send signal(%d) to pidNo = %d!\n", abs(sigNo), pidNo);
96 HILOG_ERROR(LOG_CORE,
"Kill fail ret = %d! Operation not permitted\n", ret);
100 PRINT_ERR(
"\n Kill fail ret = %d! process not exist or sigNo is invalid\n", ret);
104 PRINT_ERR(
"\nPara number errno!\n");
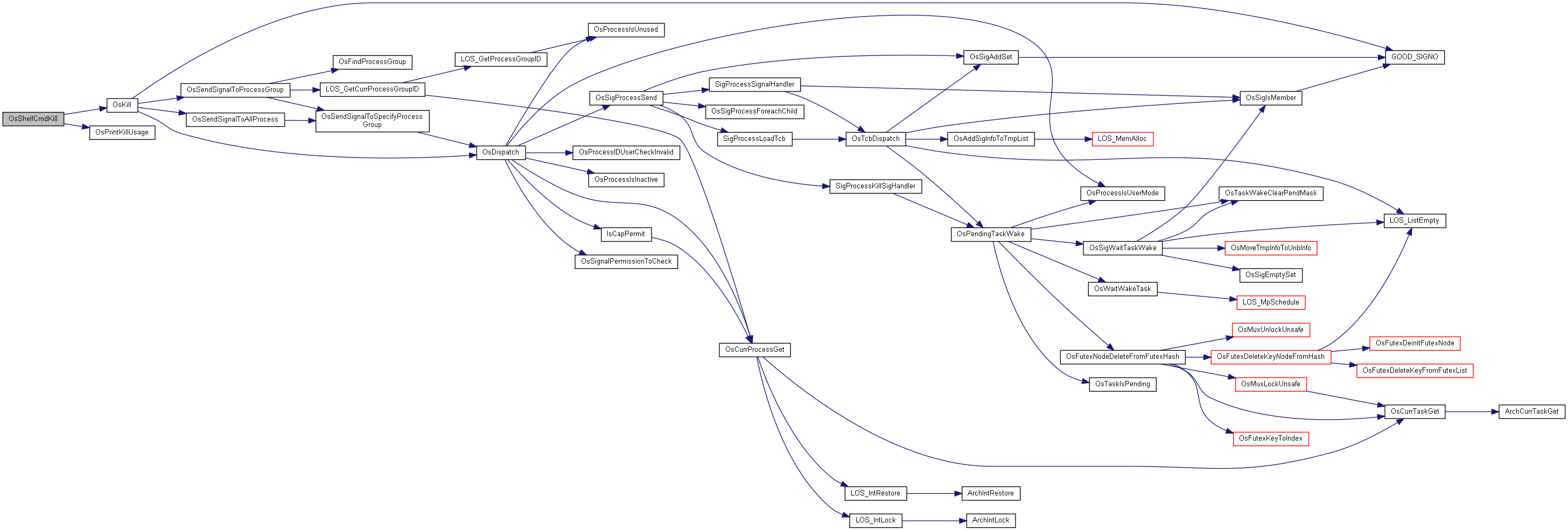
LITE_OS_SEC_TEXT_MINOR VOID OsPrintKillUsage(VOID)
int OsKill(pid_t pid, int sig, int permission)